Understanding OPSEC: A Comprehensive Guide
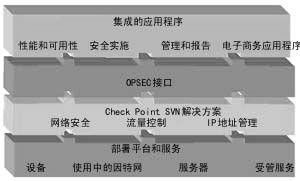
OPSEC, or Operational Security, is a critical aspect of maintaining the security and integrity of sensitive information. Whether you’re a government official, a corporate executive, or an individual looking to protect your personal data, understanding OPSEC is essential. This guide will delve into the various dimensions of OPSEC, providing you with the knowledge to safeguard your information effectively.
What is OPSEC?
OPSEC is the process of identifying and protecting sensitive information to prevent unauthorized access and use. It involves analyzing potential threats and vulnerabilities and implementing measures to mitigate them. By understanding OPSEC, you can ensure that your information remains secure and confidential.
Key Components of OPSEC
OPSEC is composed of several key components that work together to protect sensitive information. These components include:
| Component | Description |
|---|---|
| Information | The information that needs to be protected, such as classified documents, personal data, or trade secrets. |
| Threats | The potential adversaries or entities that may seek to access or exploit the information. |
| Vulnerabilities | The weaknesses in systems, processes, or personnel that could be exploited by threats. |
| Countermeasures | The actions taken to mitigate vulnerabilities and protect information. |
Identifying Threats and Vulnerabilities
One of the first steps in implementing OPSEC is to identify potential threats and vulnerabilities. This involves analyzing the information you wish to protect and considering who may be interested in accessing it. Common threats include competitors, hackers, and insiders. Vulnerabilities can arise from a variety of sources, such as weak passwords, outdated software, or inadequate security training.
Implementing Countermeasures
Once you have identified potential threats and vulnerabilities, the next step is to implement countermeasures. These measures can include:
-
Physical security: Locking doors, securing computers, and using surveillance cameras to deter unauthorized access.
-
Technical security: Implementing firewalls, encryption, and intrusion detection systems to protect information from cyber threats.
-
Administrative security: Establishing policies and procedures for handling sensitive information, such as access controls, training, and incident response.
Training and Awareness
One of the most critical aspects of OPSEC is training and awareness. Employees, military personnel, and other individuals who handle sensitive information must be educated on the importance of OPSEC and the specific measures they should take to protect information. This can include workshops, online courses, and regular reminders about security best practices.
OPSEC in Different Contexts
OPSEC is applicable in various contexts, including:
-
Government and military: Protecting classified information and ensuring the security of operations.
-
Corporate: Safeguarding trade secrets, intellectual property, and customer data.
-
Personal: Protecting personal information, such as financial data and medical records.
Conclusion
OPSEC is a vital component of protecting sensitive information in today’s interconnected world. By understanding the key components of OPSEC, identifying threats and vulnerabilities, implementing countermeasures, and ensuring training and awareness, you can effectively safeguard your information and maintain the security and integrity of your organization or personal data.
